How do you balance the necessity of highly secure passwords with the utility of easily recalling them all?
It’s a question I mull each and every time a security breach happens. When the Heartbleed vulnerability was discovered last spring, the mandate was for everyone to change all their passwords right away. It’s still on my to-do list. I cringe at the thought of getting hacked, and I also cringe at the thought of taking the time and mental energy to do a complete overhaul of my favorite passwords.
Does this sound like you?
If you happen to have a system in place to manage your unique, random, unbreakable passwords, then my hat’s off to you. According to some estimates, you are among a well-protected 8 percent of users who do not reuse passwords.
The rest of us are still searching for a solution. We know that creating a safe password is paramount, but how does one actually go about creating and recalling all those essential, random passwords we need? It took writing this post to get me on the straight-and-narrow with my passwords. Here’s what I learned about how to create a secure password you can remember.
The anatomy of an unbreakable password
The longer the password, the harder it is to crack. Consider a 12-character password or longer.
Things to avoid: Names, places, dictionary words.
Mix it up. Use variations on capitalization, spelling, numbers, and punctuation.
These three rules make it exponentially harder for hackers to crack your password. The strategies employed by password crackers have advanced to an incredibly efficient level, so it’s imperative to be unusual with the passwords you create. Here’s an example from security expert Bruce Schneier about just how far password crackers have come:
Crackers use different dictionaries: English words, names, foreign words, phonetic patterns and so on for roots; two digits, dates, single symbols and so on for appendages. They run the dictionaries with various capitalizations and common substitutions: “$” for “s”, “@” for “a”, “1” for “l” and so on. This guessing strategy quickly breaks about two-thirds of all passwords.
Recent password breaches at sites like Adobe have shown how insecure many of our passwords are. Here is a list of the most common passwords that turned up in the Adobe breach. It probably goes without saying: Avoid using these passwords.
123456
123456789
password
admin
12345678
qwerty
1234567
111111
photoshop
123123
1234567890
000000
abc123
1234
adobe1
macromedia
azerty
iloveyou
aaaaaa
654321
If you’re curious whether your chosen password is secure or not, you can run it through an online password checker like the one at OnlineDomainTools. To highlight the importance of a lengthy, random, unique password, the online checker has specific fields to show your password’s variation in characters, its appearance in dictionaries, and the time it would take for a brute force attack to crack it. Here’s an example with a password like bre7E$ret98:!aZ.
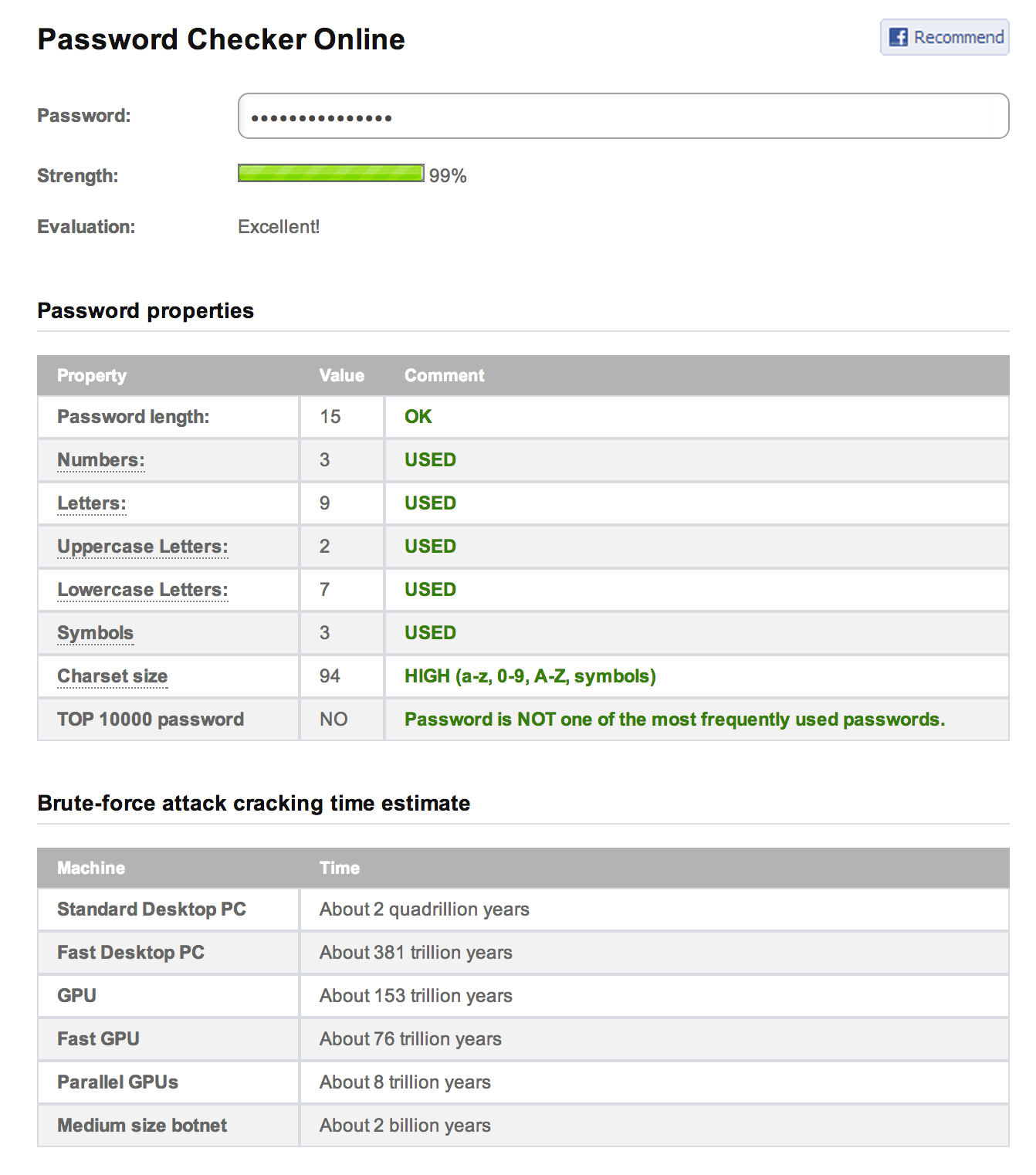
4 methods for choosing an unbreakable password
The only problem with coming up with a random, unbreakable password is that random passwords are hard to remember. If you’re solely typing in characters with no rhyme or reason—a truly random fashion—then you’ll likely have as hard a time remembering it as someone will cracking it.
So it makes sense to go with a seemingly random password, one that is near impossible for cracking software to recognize but that has meaning or familiarity for you. Here are four methods to try.
Bruce Schneier’s method
Security expert Bruce Schneier put forth a password method back in 2008 that he still recommends today. It works like this: Take a sentence and turn it into a password.
The sentence can be anything personal and memorable for you. Take the words from the sentence, then abbreviate and combine them in unique ways to form a password. Here are four sample sentences that I put together.
WOO!TPwontSB = Woohoo! The Packers won the Super Bowl!
PPupmoarT@O@tgs = Please pick up more Toasty O’s at the grocery store.
1tubuupshhh…imj = I tuck button-up shirts into my jeans.
W?ow?imp::ohth3r = Where oh where is my pear? Oh, there.
The Electrum Method
Managing a Bitcoin wallet requires a high level of security and a huge reliance on safe passwords. Enter Electrum. The Electrum wallet offers a 12-word seed that lets you access all your Bitcoin addresses. The seed serves as a master password for your Bitcoins.
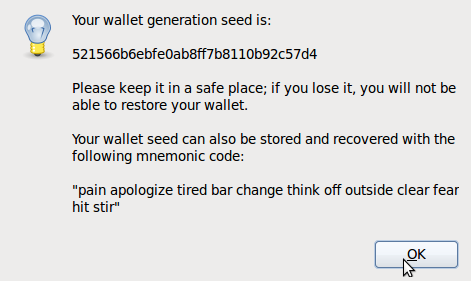
This type of password is also called a pass phrase, and it represents a somewhat new way of thinking about security. Instead of a difficult-to-remember string of characters, you can make a lengthy phrase instead. (Note: Bruce Schneier warns that password crackers now put together common dictionary words in their guesses, so if you try the pass phrase method, keep it as long as possible.)
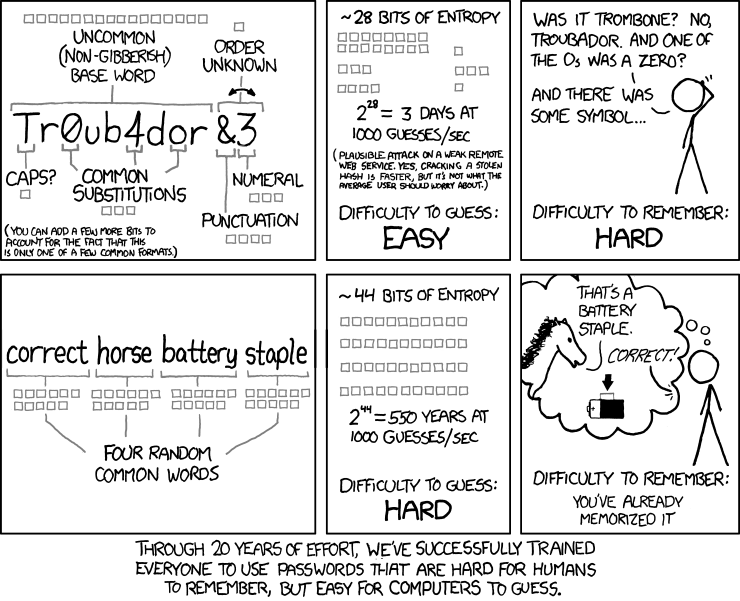
The idea for pass phrases is captured quite nicely in this comic from xkcd:
How can you create a 12-word seed of your own? It’s as simple as it sounds. Come up with 12 random words.
You can start with a phrase such as “Even in winter, the dogs party with brooms and neighbor Kit Kats.” Just make sure it is not a simple phrase or a phrase taken from existing literature. You can grab 12 random words, too: “Pantry duck cotton ballcap tissue airplane snore oar Christmas puddle log charisma.”
When placed into a password checker, the 12-word pass phrase above shows that it will take 238,378,158,171,207 quadragintillion years for a brute force attack to crack.
The PAO Method
Memorization techniques and mnemonic devices might help you remember an unbreakable password. At least, that’s the theory put forth by Carnegie Mellon University computer scientists who suggest using the Person-Action-Object (PAO) method to create and store your unbreakable passwords.
PAO gained popularity in Joshua Foer’s bestselling book Moonwalking with Einstein. The method goes like this:
Select an image of an interesting place (Mount Rushmore). Select a photo of a familiar or famous person (Beyonce). Imagine some random action along with a random object (Beyonce driving a Jello mold at Mount Rushmore).
The PAO method of memorization has cognitive advantages; our brains remember better with visual, shared cues and with outlandish, unusual scenarios. Once you create and memorize several PAO stories, you can use the stories to generate passwords.
For example, you can take the first three letters from “driving” and “Jello” to create “driJel.” Do the same for three other stories, combine your made-up words together, and you’ll have an 18-character password that’ll appear completely random to others yet familiar to you.
Phonetic Muscle Memory
I’ve developed a bit of a fondness for a personal password system of mine that I’ve used to create some strange, unusual, random passwords over time. My method relies on a couple of helpful remembering devices: Phonetics and muscle memory. Here’s how it works:
Go to a random password generator site.
Create 20 new passwords that are at least 10 characters in length and include numbers and capital letters (and punctuation if you’re feeling brave).
Scan the passwords, looking for phonetic structure—basically try to find passwords that you can sound out in your head. Ex.,
drEnaba5Et (doctor enaba 5 E.T.)
BragUtheV5 (brag you the V5)
Type out the phonetic passwords in a text file, taking note of how easy they are to type and how quickly you can type them. The easy-to-type passwords tend to get stuck in my muscle memory quicker.
Keep the phonetic, muscle-memory passwords. Toss the rest. Print out your text file with password keepers.
One at a time, change your passwords on your most-commonly-used websites. It’ll take a time or two of typing in these new passwords before you have the new them fully memorized, but typing it in enough should cement it in your brain. I still remember passwords from years ago based on this method.
The next most important step for a secure password
After creating your super-secure password, there is still one huge, all-important step remaining: Never reuse the same password.
Oof. I imagine a lot of folks get hung up on this part. Creating and remembering a unique password is challenging on its own, much less doing it multiple times. I seem to sign up at a new website or service once per day. That’s 30 new passwords a month, and I’m afraid my brain cannot hold all that in.
How do you manage to create unique passwords, never reuse a single one, and still log in with speed and efficiency (and without hitting the “forgot password” link)?
This is where the question of security vs. usability really hits home for me. Fortunately, there are a number of different approaches you can take to solving this conundrum.
Sign up for a password management tool
Your best bet with password security is to sign up for a tool like LastPass or 1Password. These tools will store your passwords for you (and even provide random new passwords when needed). All you need to do is remember a single master password that grants you access to the stored data. Enter your master password once, and the password management tool does the rest.
Some of these password management tools integrate nicely within your browser or even on a mobile device. The encrypted data is stored safely (the tools are as safe as you can get online) and passwords are retrieved easily. In almost every instance, a password manager is the best way to go, and you might only notice inconveniences when you’re logging in from a foreign device or a spot where you can’t access the service (truly rare instances).
Keep original passwords for your most important tools, apps, and websites
Another strategy I’ve come across is to max out your memory by storing as many possible passwords in your head. Use original ones for important sites like email, Facebook, Twitter, and banks. Use a common (but hard to crack) password for all the less important spots.
The risk here, of course, is that if one of your less important spots gets compromised, they’ll all be at risk. Your all-important email, social, and money accounts will be safe, which is great. Your hacked Disqus account could be posting about how much you love acai fruit, which isn’t so great.
Hybrid: Password management plus memorization
What if you mixed the two methods? Memorize passwords for your most important and most frequently used tools and use LastPass or 1Password for the rest.
You could even split it in such a way that you memorize passwords you use most often in places where LastPass and 1Password are least accessible—mobile apps you log in to all the time, for instance.
Other advice on solid, secure password management
If a site offers two-factor authentication, use it. With two-factor authentication, you receive a text message when you try logging in from a new computer.
If you have to share a password, use a site like OneTimeSecret. The site creates a link to a page with your password info (or whatever info you choose, really), and once the page is viewed once, it is gone forever.
Don’t save passwords or use “remember me” on public computers.
Keep written passwords stored securely. Consider keeping them in a safe or a safe-deposit box so that they’ll only be accessed by those who need to know.
Don’t change your passwords, unless you suspect they’ve been compromised. Changing your password regularly does not have an effect on the likelihood of it being cracked.
What have you learned about password management?
I’d love to hear any tips you have about the best methods for creating a secure password (and storing and accessing those passwords). What tools do you use? How many are you able to memorize at once? (I max out around five.) Share your thoughts here in the comments.
P.S. If you liked this post, you might enjoy our Buffer: Open Blog newsletter. Receive each new post delivered right to your inbox! Sign up here.
Image credit: loryan, bitcointalk, xkcd
Try Buffer for free
190,000+ creators, small businesses, and marketers use Buffer to grow their audiences every month.



